Preventing Fraudulent Activities by enabling robust Security Controls
In today’s digital landscape, fraudulent activities pose significant risks to organisations of all sizes. From data breaches, breach of law and phishing scams to unauthorised access and insider threats creating potential impact on sensitive data and network infrastructure is immense. Implementing robust security controls is essential for protecting both data and network resources, ensuring business continuity, and maintaining stakeholder trust.
Fraudulent activities encompass a wide range of malicious actions intended to trick, steal, or compromise an organisation’s assets or individual’s account. Some of key examples are:
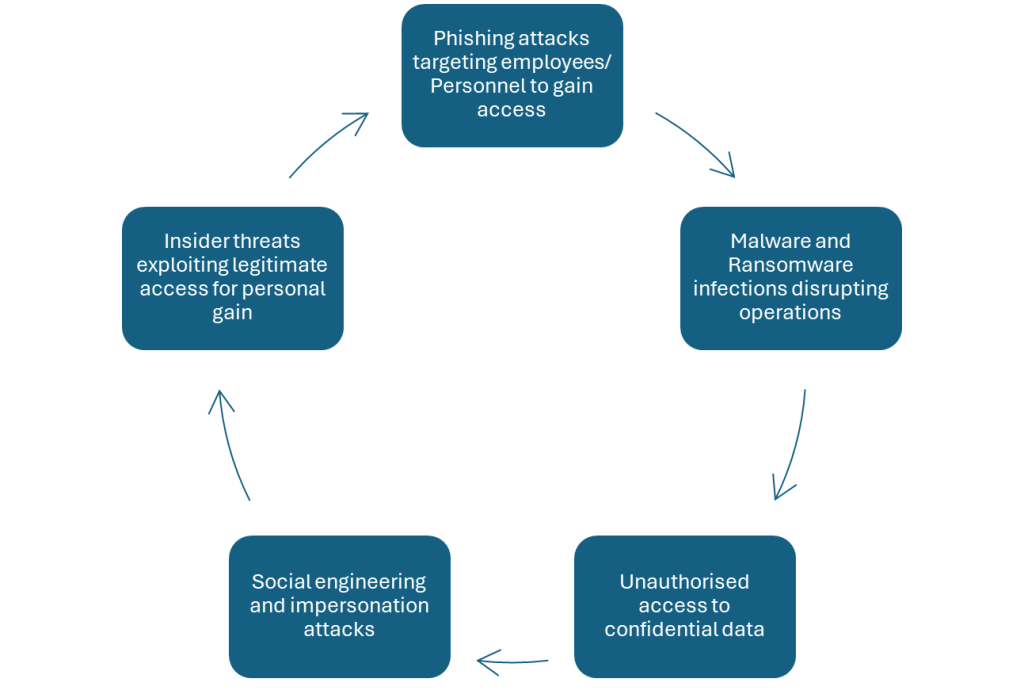
The impact of fraudulent activities on businesses can be expensive and difficult to handle without secured controls in place to reduce the threat or to minimize the impact. Financial losses are often the most immediate consequence, stemming from theft of funds, fraudulently obtained goods, or the costs associated with responding to and recovering from incidents. Beyond direct financial damage, organisations may also face significant reputational harm, which can end up in loosing customer trust and deter potential clients or partners.
Operational disruption is another major concern, as fraudulent activities such as ransomware attacks can halt critical business processes and lead to downtime. Additionally, businesses may incur regulatory penalties or legal liabilities if data breaches involve sensitive personal or financial information. Ultimately, the emerging effect of these impacts can threaten the long-term viability of an organisation, underscoring the importance of robust security controls and proactive risk management strategies.
Key Security Controls for Protect and Secure the Environment:
Organisations must implement a layered approach to security and enable stringent monitoring systems to prevent evolving fraudulent activities day by day.
Some of the essential security controls that safeguards data and networks are:

-
Access Control and Authentication
- Restricting access to sensitive systems and data is a foundational security principle
- Require multiple forms of verification (PAM/MFA) before granting access to sensitive systems or data.
- Limit user access based on job responsibilities (RBAC), ensuring individuals only access necessary data.
- Separate critical functions (e.g: approval and execution of payments) to prevent a single individual from having complete control over sensitive processes.
- Removing access promptly when an employee leaves the organisation or changes roles, reducing the window of opportunity for fraud.
- Periodically audit and update user permissions to prevent privilege creep.
-
Network Security Measures
- Deploy firewalls to monitor and control incoming and outgoing network traffic based on predetermined security rules.
- Restrict network access to sensitive systems and data using firewalls, access control lists (ACLs), and network segmentation.
- Implement least privilege principles, ensuring only authorised users and processes can access or manipulate pointer-sensitive operations.
- Detect and block suspicious activities or policy violations in real time.
- Monitor for unusual access patterns that may signal attempts to exploit vulnerabilities
- Divide the network into distinct zones to contain potential breaches and restrict lateral movement.
-
Endpoint and Application Security
- Install and regularly update protective software on all endpoints.
- Ensure all endpoints are equipped with reputable antivirus and anti-malware solutions that are regularly updated.
- EDR/XDR tools to monitor endpoint activity, detect suspicious behaviour, and provide rapid response capabilities.
- Adopt secure coding practices to minimise vulnerabilities such as SQL injection, cross-site scripting (XSS), and buffer overflows.
- Limit endpoint access to sensitive resources based on user roles and device compliance.
- Ensure sensitive data is encrypted in transit and at rest, and implement proper data handling policies.
- Allow only approved applications to run, reducing the risk of malicious software execution.
-
Security Awareness and Training
- Fostering a culture of security awareness is crucial for preventing fraudulent activities within the organisation.
- Regularly educate staff about the latest threats, safe online practices, and how to recognise suspicious activities.
- Conduct simulated attacks to test and improve employee vigilance.
-
Monitoring and Incident Response
- Use Security Information and Event Management (SIEM) systems to monitor network activity for anomalies.
- Monitoring user actions to detect deviations from normal patterns, which may indicate fraudulent intent.
- Develop and regularly test a response plan to swiftly contain and mitigate security incidents.
- Conducting routine checks of system logs, access controls, and financial records to uncover hidden issues.
- Use monitoring tools to detect incidents promptly. Analyse incident data to determine the nature and extent of the fraud.
- Investigate incidents thoroughly to understand the root cause and prevent recurrence.
Best Practices for Ongoing Protection:
- Implement a Zero Trust security approach, regardless of whether they are within or outside the network boundaries.
- Regularly update and test security policies and procedures.
- Engage in threat intelligence sharing with industry peers.
- Conduct regular security assessments and penetration testing.
- Maintain compliance with relevant regulations and standards (e.g., GDPR, ISO 27001).
- Continuous Training and Awareness as the shield for protecting ourselves from emerging threats
Preventing fraudulent activities requires a comprehensive and proactive measures to secure the environment. By developing, implementing, and maintaining robust security controls, organisations can significantly reduce their exposure to threats and protect their data in this emerging threat landscape.
Written by: Kavitha Srinivasulu
Company: TCS
Designation: Program Director–Cyber Security & Data Privacy : BFSI
About the Author: Experienced Cybersecurity and Data Privacy Leader with overall 22 years of experience focused on Risk Advisory, Data Protection and Business Resilience. Demonstrated expertise in identifying and mitigating risks across ISO, NIST, SOC, CRS, GRC, RegTech and in emerging technologies with diverse experience across corporate and Strategic Partners. Possess a solid balance of domain knowledge & smart business acumen ensuring business requirements and organizational goals are met.
Disclaimer:
“The views and opinions expressed by Kavitha in this article are solely her own and do not represent the views of her company or her customers.”

